There are different ways to login to ALICE or SHARK from Windows. This page contains instructions for various applications that provide a command line interface to ALICE and SHARK, but you can also get a complete remote desktop on both clusters using X2Go.
Overview
The following table gives an overview of the main features that are available for the applications described below.
Application | Command line interface | Integrated X11 forwarding | Full remote desktop | File Transfer from local workstation | Password-less login with standard SSH keys | Password-less login with PuTTY ssh keys (and PuTTY pageant) |
|---|---|---|---|---|---|---|
|
|
|
|
|
| |
|
|
|
|
|
| |
|
|
|
|
|
| |
|
|
|
|
|
| |
| not necessary |
|
|
|
| |
WinSCP (primarily suited for data transfer) |
|
|
|
|
|
|
PowerShell
For Windows 10 build 1809 and higher, OpenSSH is available for PowerShell. This allows you to use PowerShell to connect to ALICE using ssh without any additional third-party tools for most purposes.
While PowerShell has its own syntax and commands, it is possible to use certain Linux commands within PowerShell.
Check if you already have OpenSSH installed. You can open PowerShell for example by opening the start menu and start typing "PowerShell". Under "Apps", you should see "Windows PowerShell". Start it and type
ssh -V
This should show the version of OpenSSH that you are using. If it does not work, then install OpenSSH for PowerShell before continuing.
Do you need multiple command line sessions?
There is also a tool called Windows Terminal which allows you to use different command line environments on Windows including PowerShell. Windows Terminal allows to open multiple command line sessions as tabs.
Except for the limitations listed below, using ssh with PowerShell works in the same way as on Linux
Known Limitations
It is currently not possible to do X11 forwarding natively with PowerShell
The command
ssh-copy-idis not available, but you can copy the keys manuallyOnly
scpis available in PowerShell
First time users
If you are a first time user, we recommend to go through the corresponding section for Linux users: https://pubappslu.atlassian.net/wiki/spaces/HPCWIKI/pages/37748788/Login+to+ALICE+or+SHARK+from+Linux#For-first-time-users-or-%E2%80%9Cthe-most-basic-way%E2%80%9D
Regular users
If you decide to use PowerShell on a regular basis, we recommend that you setup your ssh config. You can also make use of password-less login using ssh keys with PowerShell.
SSH config setup
While syntax and usage of the ssh config file is the same as for Linux users, creating the ssh config file requires some additional steps on Windows.
Text editors on Windows
For working with a Linux-based cluster such as ALICE or SHARK from Windows, we recommend to install an alternative text file editor. The main reason is that the editor needs to be able to save text files with the line ending properly formatted for Linux. Windows (including the build-in notepad editor) encodes line endings in a different way which can lead to issues when such text files are read or executed on the cluster. There is a great variety of applications freely available. Prominent examples are "Notepad++" and "Visual Studio Code".
First, you need to make sure that you have a directory called “.ssh” in your home directory on Windows which is usually something like C:\Users\<YOUR_WINDOWS_USERNAME>. You can check this using PowerShell:
PS C:\> cd $HOME PS C:\> ls .ssh
If the directory “.ssh” directory does not exists, create it for example with the File explorer or with PowerShell.
PS C:\Users\me> mkdir .ssh
Next, you need to create a text file called “config” in the “.ssh” directory and add the ssh config settings for ALICE or SHARK as described here: https://pubappslu.atlassian.net/wiki/spaces/HPCWIKI/pages/37748788/Login+to+ALICE+or+SHARK+from+Linux#For-regular-users-or-%E2%80%9Cthe-more-elegant-way%E2%80%9D
The name of the file “config” cannot have a file ending, i.e., it cannot be called something like “config.txt”.
Saving a file without file ending is straightforward with alternative editors such as “Notepad++” or “Visual Studio Code”, but not with the build-in notepad editor. Alternatively, you can also user PowerShell to rename the file by running for example mv config.txt config
Password-less login with ssh keys
Password-less login with ssh keys is possible with PowerShell. However, the procedure is slightly different from Linux described in https://pubappslu.atlassian.net/wiki/spaces/HPCWIKI/pages/37748788/Login+to+ALICE+or+SHARK+from+Linux#Making-logins-even-more-convenient-with-ssh-keys because the command ssh-copy-id is not available.
First, create an ssh config as described in the previous section.
Second, create a set of ssh keys with ssh-keygen.exe (see https://pubappslu.atlassian.net/wiki/spaces/HPCWIKI/pages/138182663/SSH+Keys#Using-Windows-OpenSSH-client).
Once you have a set of keys, you need to copy the public key manually to the .ssh/authorized_keys file in your home directory on the ssh gateway and on one of the login nodes. This can be done for example like this from within PowerShell:
first, we have to add the public key on the gateway. SHARK users can skip this step if they are only working from within the LUMC network. ALICE users always have to do this.
type $env:USERPROFILE\.ssh\id_rsa.pub | ssh <GATEWAY> "cat >> .ssh/authorized_keys"
where you need to replace
$env:USERPROFILE\.sshby the correct path if you are not using the default path and<GATEWAY>by the host name of the ssh gateway from ALICE or SHARK (see https://pubappslu.atlassian.net/wiki/spaces/HPCWIKI/pages/37748788/Login+to+ALICE+or+SHARK+from+Linux#For-first-time-users-or-%E2%80%9Cthe-most-basic-way%E2%80%9D)Next, we add the public key on one of the login nodes. Here, we assume that you have set up an ssh config
type $env:USERPROFILE\.ssh\id_rsa.pub | ssh <SSH_CONFIG_HOST> "cat >> .ssh/authorized_keys"
where you need to replace
$env:USERPROFILE\.sshby the correct path if you are not using the default path and<SSH_CONFIG_HOST>by the host alias specified in the ssh config for ALICE or SHARK (e.g.,alice1orshark1)
If you are not using the default name for your ssh key, then you need to adjust your ssh config settings as described here: https://pubappslu.atlassian.net/wiki/spaces/HPCWIKI/pages/37748788/Login+to+ALICE+or+SHARK+from+Linux#Using-ssh-keys-with-custom-names
Windows Subsystem for Linux
If you have installed the Windows Subsystem for Linux (WSL), you can follow the instructions on Login to ALICE or SHARK from Linux in order to setup your connection.
Known Limitations
It is currently not possible to do X11 forwarding natively with WSL.
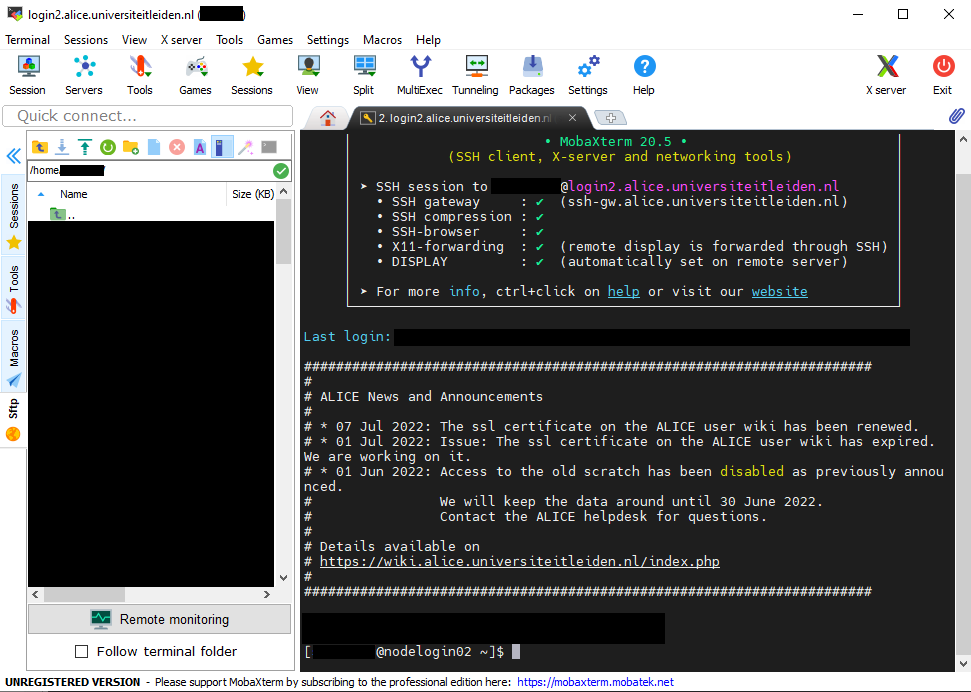
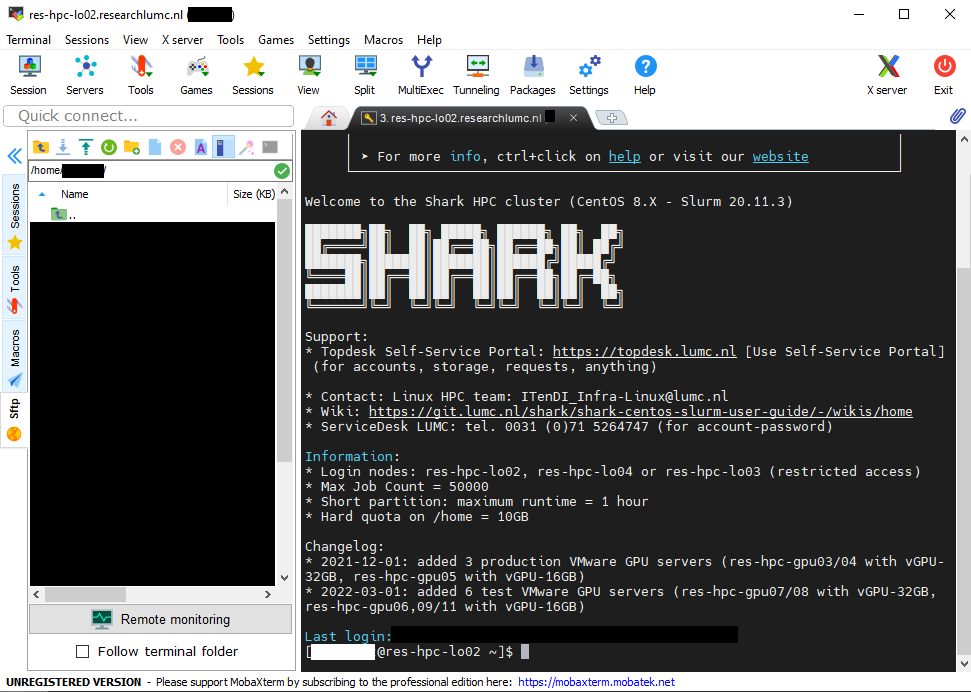
MobaXTerm
With MobaXTerm, you have a build-in SSH shell/terminal, an embedded X11 server, and a file explorer that allows drag-in-drop for moving files to and from the cluster. With this, you do not have to worry about setting up a special X11 server for showing graphical output on your Windows workstation or an alternative program for moving files.
First, go to the MobaXterm website: MobaXterm and download the latest version (here is the direct download link: Download). You can either install it on your local workstation or get the portable version.
Password-less login with ssh keys in MobaXTerm.
While you do not have set up password-less login with ssh keys in MobaXTerm to log in to the cluster, you need to do it since version 24.1 of MobaXTerm if you want to use the integrated file browser.
If you have not created ssh keys yet on Windows, you can find instructions here: SSH Keys - HPC wiki (atlassian.net). With MobaXTerm, you can use OpenSSH-like keys (such as created with PowerShell) or PuTTY-style keys (such as with PuTTY or the MobaXTerm key generator).
Once you have generated a set of ssh keys, you have to copy the public key over to the ssh gateway and one of the login nodes. SHARK users only need to put the key on the LUMC ssh gateway if they want to access SHARK from outside the LUMC network.
Important: Do not copy the private key to the cluster. The private key should never be shared and remains on your local computer. You only have to copy the public key to the cluster.
The following instructions outline how to copy the public ssh key to the cluster using MobaXTerm itself though you can also use other means outlined in previous sections.
First, click on the “+”-icon in the tab bar to open a local session. What we do in this session is not persistent, but this is fine for us. As noted in the banner message, your local drives are available in this session, which means that we can access the public key.
Next, we will copy the public and private key to the
.sshdirectory in the temporary local MobaXTerm session. Once the session is closed, the files will be removed, but this is fine because we only need to do this to copy them over to the cluster. While you can also access the ssh keys on your local drives directly, using them for the following commands has the tendency to mess up some file permissions on the keys which have to be sorted out afterwards.
You can copy the keys like this:cp /drives/c/Users/<username>/.ssh/<file_name_of_private_key> ./.ssh/ cp /drives/c/Users/<username>/.ssh/<file_name_of_public_key> ./.ssh/
where you have to replace
<username>by the user name on Windows,<file_name_of_private_key>by the name of the file with the private key and<file_name_of_public_key>by the name of the file with the public key. Note that the command above that you used the default location to store your ssh key on Windows, if not, please adjust the path accordingly.Next, we will put the ssh key on the ssh gateway. ALICE users will always have to do this step, but LUMC users need to do this only if they want to access SHARK from outside the LUMC network.
If you used MobaXTerm or PuTTY to generate the keys, please continue to the next step (2b). If you have created OpenSSH-style ssh keys, you can use the command “ssh-copy-id”.
Type in the following command
ssh-copy-id -i .ssh/<file_name_of_private_key> <alice/shark_username>@<ssh-gateway>
where you have to replace
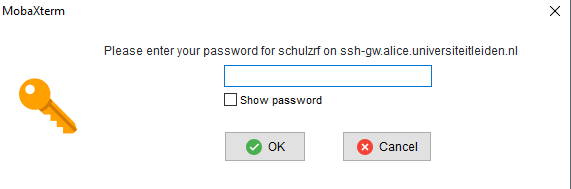
<file_name_of_private_key>by the name of the file with the private key,<alice/sharek_username>by your ALICE or SHARK username and<ssh_gateway>by the name of the ssh gateway used by ALICE (ssh-gw.alice.universiteitleiden.nl) or SHARK (res-ssh-alg01.researchlumc.nl).After confirming with enter, you will first be asked to confirm the identity of the gateway and then to provide your password. If the password authentication is successful, your key should have been copied and you can continue with step 3.
For keys generated with PuTTY or MobaXTerm, the process is slightly different.
First, open “MobaKeyGen” from the “Tools menu
In the new window, click on “load” and open the private ssh key that you want to use.
The grey box “Key” should now show you the public key that you can use for pasting into the
~/.ssh/authorized_keysfile on the gateway.You can use the following command to copy the public key to the ssh gateway
MYPUBLICKEY="<public_ssh_key" ssh <alice/shark_username>@<ssh_gateway> "echo $MYPUBLICKEY >> ~/.ssh/authorized_keys"
where you have to replace
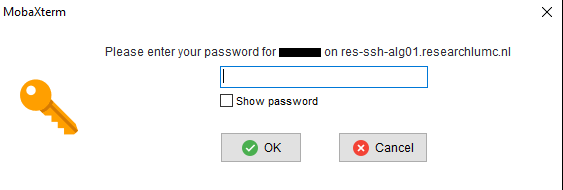
<public_key>by the text displayed in “Public key for pasting into OpenSSH server” in the MobaKeyGen window,<alice/sharek_username>by your ALICE or SHARK username and<ssh_gateway>by the name of the ssh gateway used by ALICE (ssh-gw.alice.universiteitleiden.nl) or SHARK (res-ssh-alg01.researchlumc.nl).After confirming with enter, you will first be asked to confirm the identity of the gateway and then to provide your password. If the password authentication is successful, your key should have been copied and you can continue with step 3.
This step is just to confirm that the ssh key was successfully copied over. If you do not want to do it, you can go to step 4.
Run the following command to login to the ssh gateway
ssh -i .ssh/<file_name_of_private_key> <alice/shark_username>@<ssh_gateway> 'echo "Hello World from $(hostname)"'
where you have to replace
<file_name_of_private_key>by the name of the file with the private key,<alice/sharek_username>by your ALICE or SHARK username and<ssh_gateway>by the name of the ssh gateway used by ALICE (ssh-gw.alice.universiteitleiden.nl) or SHARK (res-ssh-alg01.researchlumc.nl).
If you encrypted your ssh key with a passphrase, you will be asked to provide the passphrase to encrypt the key.If the steps above went well, then you will not be asked for your password and you should just get the output “Hello World from …”
Now, we are ready to put the public ssh key in our home directory on one of the login nodes on the cluster.
If you used MobaXTerm or PuTTY to generate the keys, please continue to the next step (4b). If you have created OpenSSH-style ssh keys, you can use the command “ssh-copy-id” again.
Type in the following command
ssh-copy-id -i .ssh/<file_name_of_private_key> -o ProxyJump=<alice/shark_username>@<ssh-gateway> <alice/shark_username>@<alice/shark_login_node>
where you have to replace
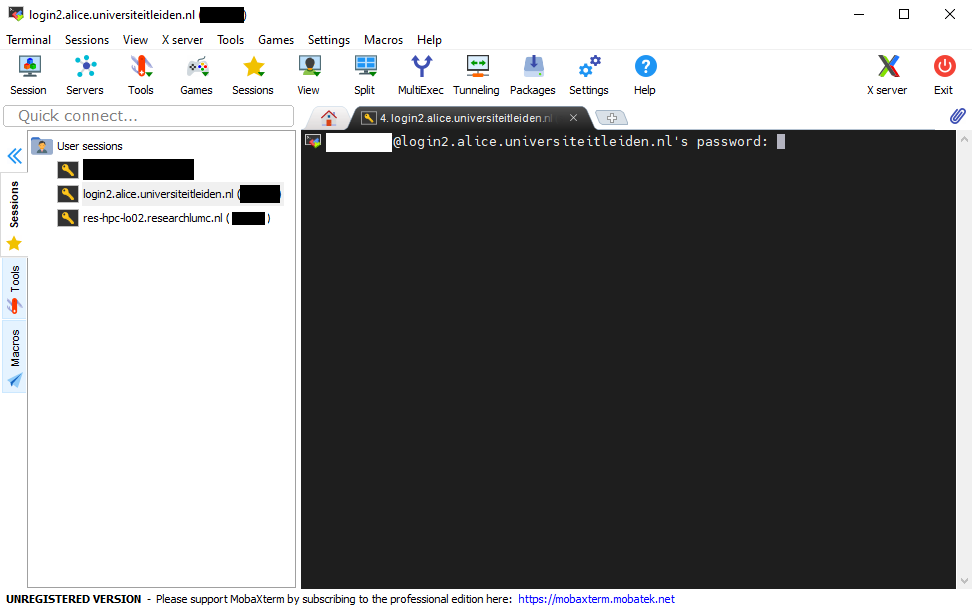
<file_name_of_private_key>by the name of the file with the private key,<alice/sharek_username>by your ALICE or SHARK username,<ssh_gateway>by the name of the ssh gateway used by ALICE (ssh-gw.alice.universiteitleiden.nl) or SHARK (res-ssh-alg01.researchlumc.nl), and<alice/shark_login_node>by one of the login nodes on ALICE (e.g.,login1.alice.universiteitleiden.nl) or SHARK (e.g.,res-hpc-lo02.researchlumc.nl).After confirming with enter, you will first be asked to confirm the identity of the login node and then to provide your password for the login. You should not be asked for a password to login at the gateway, only to for the passphrase of your private key if you encrypted the private key with it. If the password authentication on the login node is successful, your key should have been copied and you can continue with step 5.
For keys generated with PuTTY or MobaXTerm, the process is again slightly different.
First follow steps 2b-i through 2b-iii to open the key with MobaKeyGen.
You can use the following command to copy:
MYPUBLICKEY="<public_ssh_key" ssh -J ProxyJump=<alice/shark_username>@<ssh-gateway> -i .ssh/<file_name_of_private_key> <alice/shark_username>@<alice/shark_login_node> "echo $MYPUBLICKEY >> ~/.ssh/authorized_keys"
where you have to replace
<public_key>by the text displayed in “Public key for pasting into OpenSSH server” in the MobaKeyGen window,<alice/sharek_username>by your ALICE or SHARK username,<ssh_gateway>by the name of the ssh gateway used by ALICE (ssh-gw.alice.universiteitleiden.nl) or SHARK (res-ssh-alg01.researchlumc.nl),<file_name_of_private_key>by the name of the file with the public key and<alice/shark_login_node>by one of the login nodes on ALICE (e.g.,login1.alice.universiteitleiden.nl) or SHARK (e.g.,res-hpc-lo02.researchlumc.nl).
To simplify the above command, you can also run it without-i .ssh/<file_name_of_private_key>. You will just be asked for your password twice in the next step (once for the gateway) which is fine because ssh does not know about the private key.
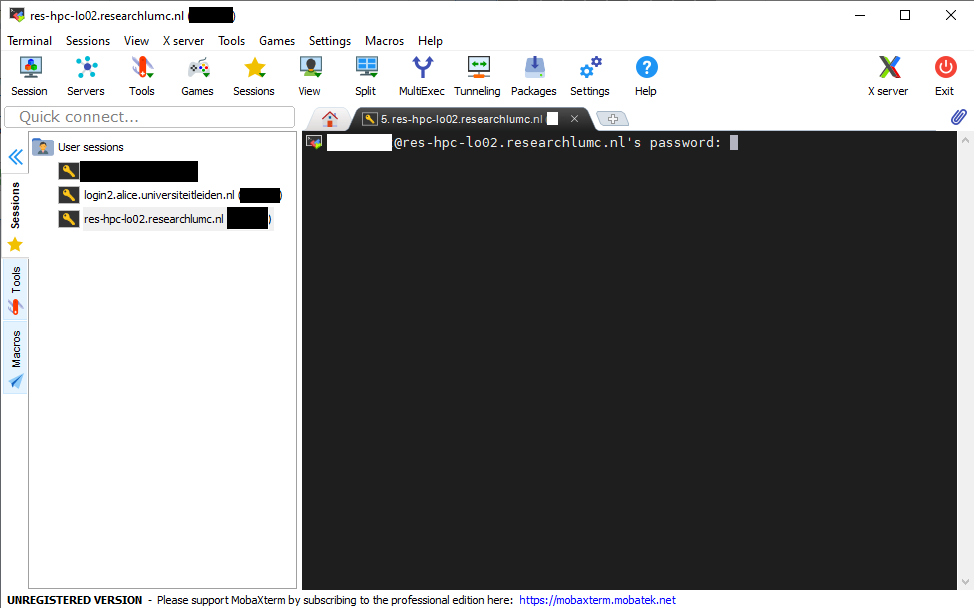
SHARK users who do not need to use the LUMC ssh gateway should run the command without-J ProxyJump=<alice/shark_username>@<ssh_gateway>After confirming with enter, you will first be asked to confirm the identity of the login node and then to provide your password. If the password authentication is successful, your key should have been copied and you can continue with step 5.
This step is just to confirm that the ssh key was successfully copied over.
Run the following command to login to one of the login nodes:
ssh -J <alice/shark_username>@<ssh-gateway> -i .ssh/<file_name_of_private_key> <alice/shark_username>@<alice/shark_login_node> 'echo "Hello World from $(hostname)"'
where you have to replace
<alice/sharek_username>by your ALICE or SHARK username,<ssh_gateway>by the name of the ssh gateway used by ALICE (ssh-gw.alice.universiteitleiden.nl) or SHARK (res-ssh-alg01.researchlumc.nl),<file_name_of_private_key>by the name of the file with the public key and<alice/shark_login_node>by one of the login nodes on ALICE (e.g.,login1.alice.universiteitleiden.nl) or SHARK (e.g.,res-hpc-lo02.researchlumc.nl).
When running this command, you will be asked for your password to login in to the ssh gateway. This is fine to simplify the setup of the command and we know from step 3 that the key is working on the gateway.
SHARK users who do not need to use the LUMC ssh gateway should run the command without-J ProxyJump=<alice/shark_username>@<ssh-gateway>If the steps above went well, then you will only be asked for the password to the ssh gateway (if you use the gateway), but not for the login node and you should just get the output “Hello World from …”
You can close the local MobaXTerm session now.
Now that the public ssh key is copied over to the cluster, you can use the key in any MobaXTerm session for the cluster.
Set up a session in MobaXTerm
Now, you can start MobaXTerm and create a SSH session:
ALICE | SHARK | |
|---|---|---|
For the session type choose: SSH and press OK | For the session type choose: SSH and press OK | |
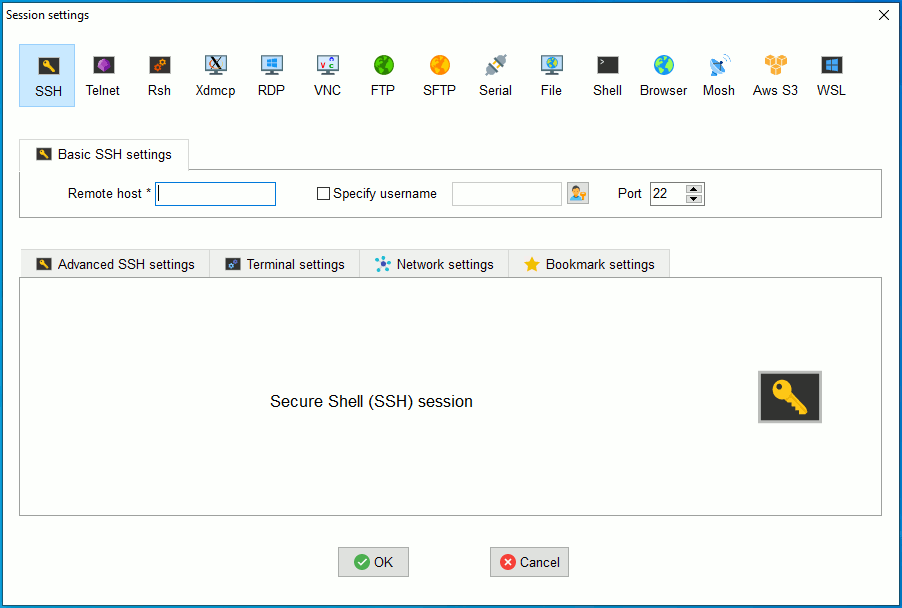
In “Basic SSH settings”, specify the following settings:
| In “Basic SSH settings”, specify the following settings:
If you intend to use this session to connect to SHARK from within the LUMC, you can finish the setup here by clicking on “OK”. Otherwise, continue here to specify certain additional settings. | |
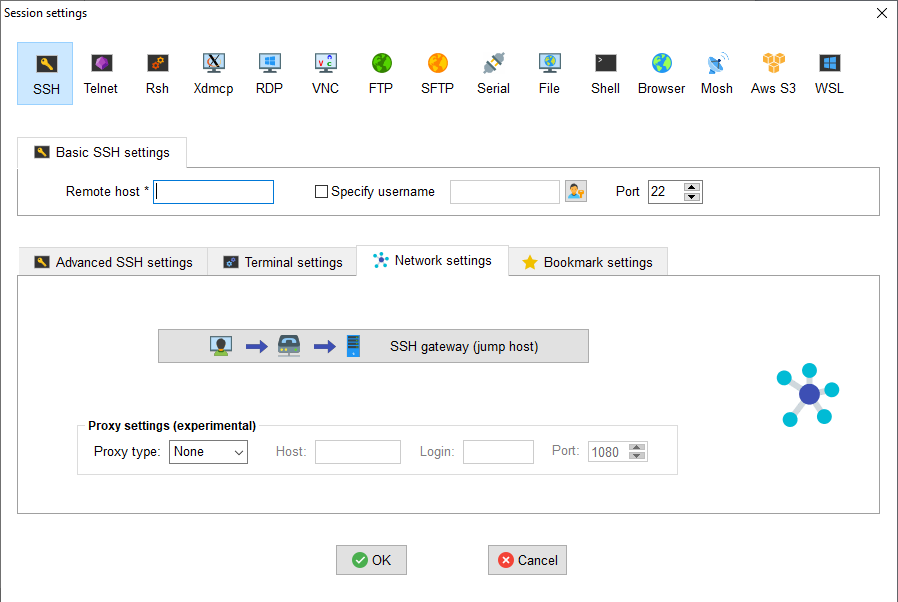
Next, click on “Network settings” and then on the button “SSH gateway (jump host) | If you want to setup a connection with MobaXTerm for connecting to SHARK from outside the LUMC, click on “Network settings” and then on the button “SSH gateway (jump host). | |
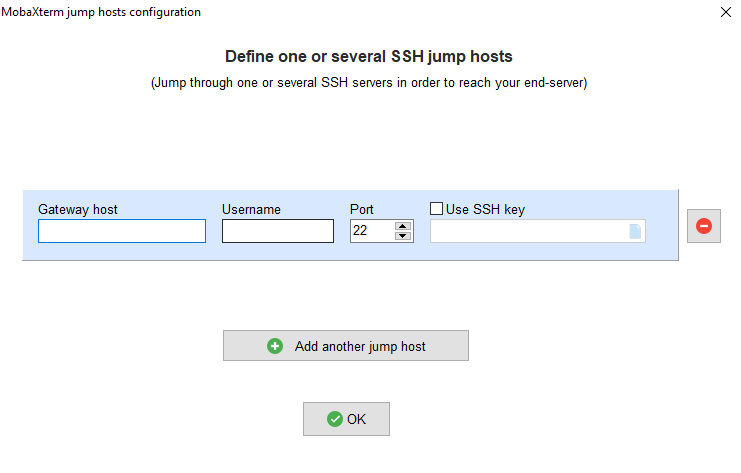
Specify the following settings:
If you have set up ssh keys for logging in to ALICE, you can tick the box next to “Use SSH key” and click on the document icon in the field which will open a file browser that you can use to set the path to the private key. While you do not have to use ssh keys to login (your password is fine), you will need use ssh keys if you want to use the integrated file browser in MobaXTerm. When all is set, confirm by clicking on “OK”. Now, you are back on the previous window. If you do not want to use ssh keys, you can finalize the setup by clicking on “OK”. Otherwise, go to the next step. | Specify the following settings:
If you have set up ssh keys for logging in to ALICE, you can tick the box next to “Use SSH key” and click on the document icon in the field which will open a file browser that you can use to set the path to the private key. While you do not have to use ssh keys to login (your password is fine), you will need use ssh keys if you want to use the integrated file browser in MobaXTerm. Then, confirm by clicking on “OK”. Now, you are back on the previous window. If you do not want to use ssh keys, you can finalize the setup by clicking on “OK”. Otherwise, go to the next step. | |
This step is only necessary if you want to use ssh keys to login. If not, you can go to the next step. Open the tab “Advanced SSH settings”. Tick the box next to “Use private key”. Click on the little document icon in the field next to it. This should open a file browser which you can use to set the path to the private key. When you are done confirm with “OK”. Using ssh keys will only work if you already put the public key on the ssh gateway and one of the login nodes. | This step is only necessary if you want to use ssh keys to login. If not, you can go to the next step. Open the tab “Advanced SSH settings”. Tick the box next to “Use private key”. Click on the little document icon in the field next to it. This should open a file browser which you can use to set the path to the private key. When you are done confirm with “OK”. Using ssh keys will only work if you already put the public key on the ssh gateway and one of the login nodes. | |
MobaXTerm will now try to connect you to ALICE. If you instructed MobaXTerm to use ssh keys in the step before, it should log you in right away and you can continue to the next step. In case you encrypted your private key with a passphrase, MobaXTerm will ask you for the passphrase. If you do not use ssh keys, MobaXTerm will first ask you to provide the password for logging in to the ssh gateway: If successful, you need to type in your password one more time to log in to the login node: Note that in contrast to the pop-up window for the login to the gateway, you will not see anything when you type in or copy-paste your password for the login node. This is completely normal when using ssh on the command line. | MobaXTerm will now try to connect you to ALICE. If you instructed MobaXTerm to use ssh keys in the step before, it should log you in right away and you can continue to the next step. In case you encrypted your private key with a passphrase, MobaXTerm will ask you for the passphrase. If you do not use ssh keys and if you set your session up to use the LUMC ssh gateway, you will be asked to provide the password for the ssh gateway first: If successful or if you directly log in to the login node, you need to type your password one more time to log in to the login node: Note that in contrast to the pop-up window for the login to the gateway, you will not see anything when you type in or copy-paste your password for the login node. This is completely normal when using ssh on the command line. | |
After a successful login, you will have a command line interface available on ALICE and to the left of it, there will be a file explorer showing you all the files in your home directory (“sftp” tab). You can navigate around in it just as you would on your local file explorer. | After a successful login, you will have a command line interface available on ALICE and to the left of it, there will be a file explorer showing you all the files in your home directory (“sftp” tab). You can navigate around in it just as you would on your local file explorer. |
In order to keep the ssh connection from breaking up after a few minutes of being idle, go to "Settings->Configuration->SSH" and enable the setting "SSH keepalive" under "SSH Settings".
From version 24.1 an above, the file browser will not open and show the content of your directory on the cluster if you login using your password. If you want to continue using the file browser, you have to set up password-less login using ssh keys.
PuTTY
PuTTY is a simple terminal ssh shell (putty homepage, putty download). PuTTY is available for installation or as a portable version.
Setting up PuTTY to use an ssh gateway server is somewhat different from logging in directly to a server. Therefore, we will provide instructions for direct access first (Connecting with PuTTY without using an ssh gateway)
If you are using ALICE or SHARK from outside the LUMC, proceed to the next section to set up PuTTY for using an ssh gateway (Connecting with PuTTY using an ssh gateway).
Connecting with PuTTY without using an ssh gateway
ALICE | SHARK | |
|---|---|---|
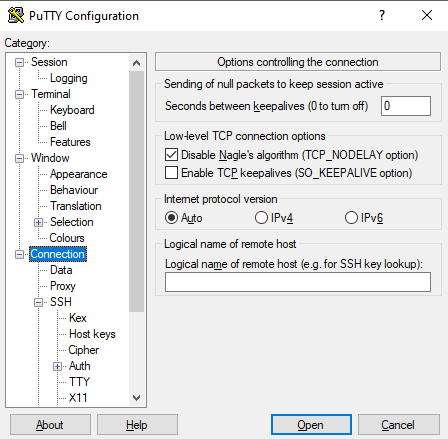
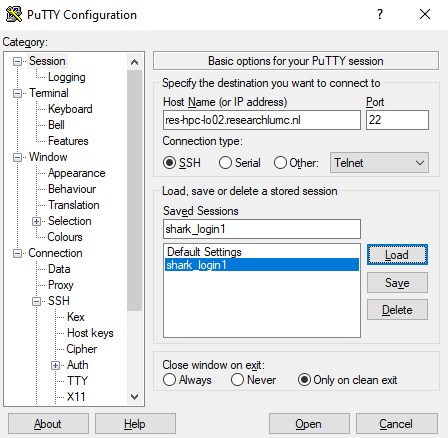
For ALICE, please see Connecting with PuTTY using an ssh gateway | After you have started PuTTY, go first to the category “Connection” and set “Second between keepalives” to 60. Otherwise the connection will automatically terminated after a few minutes. Then switch back to the category “Session” This has to be done for every connection that you want to set up. | |
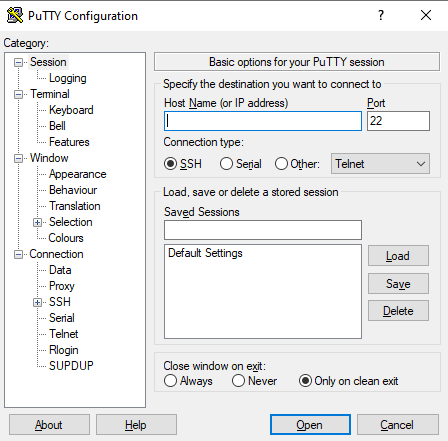
| Set as “Host Name” either We recommend that you save the settings for this session:
You can set up sessions for both login nodes. When you are finished, click on the button “Open” | |
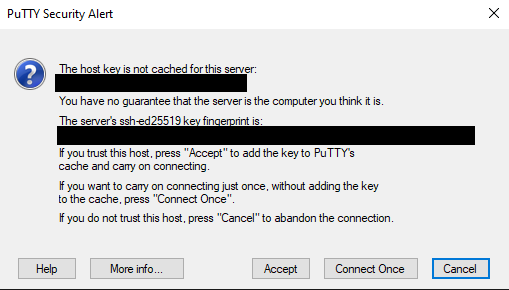
When you connect for the first time, PuTTY will raise a security alert in an overlay window. Confirm the authenticity of the server that you try to connect to by clicking “Accept”. | ||
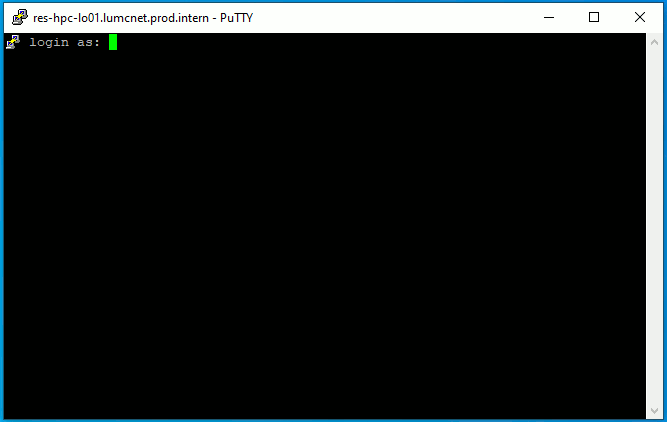
Next, specify your SHARK user name, confirm with enter. Then, PuTTY will ask for your SHARK user password. Type it in and confirm with enter. For novice users: When you type in your password, you will not see any characters appearing. It will seem as if the line is blank and you have typed nothing in. However, this is not the case. You will have typed in the password. | ||
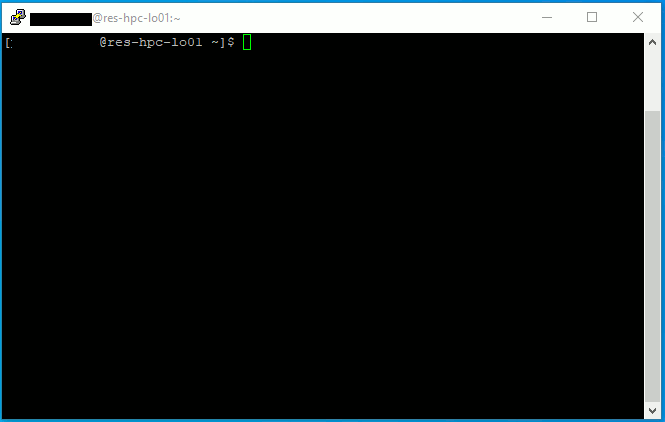
Once logged in, the command line prompt will show your SHARK username and the name of the server. You can logout by typing the command By clicking on the PuTTY symbol, you can access to additional functions of PuTTY. | ||
When you want to connect the next time, you can click on the name of the session in the list of “Saved Sessions”, click on the button “Load” and then on the button “Open”. |
Connecting with PuTTY using an ssh gateway
ALICE | SHARK | |
|---|---|---|
After you have started PuTTY, go first to the category “Connection” and set “Second between keepalives” to 60. Otherwise the connection will automatically terminated after a few minutes. Then switch back to the category “Session” This has to be done for every connection that you want to set up. | After you have started PuTTY, go first to the category “Connection” and set “Second between keepalives” to 60. Otherwise the connection will automatically terminated after a few minutes. Then switch back to the category “Session” This has to be done for every connection that you want to set up. | |
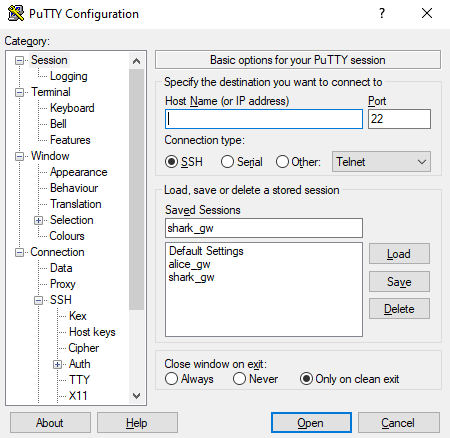
Set “Host Name” to Save the session in “Saved Session” with the name “alice_gw” and click the button “Save” | Set “Host Name” to Save the session in “Saved Session” with the name “shark_gw” and click the button “Save” | |
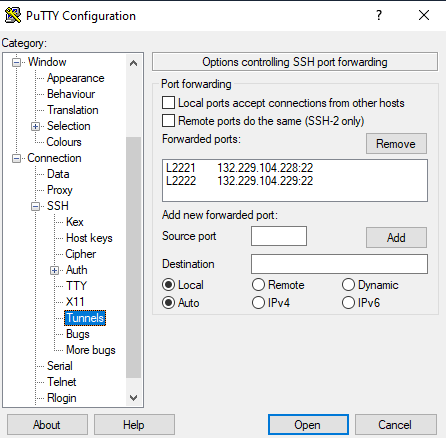
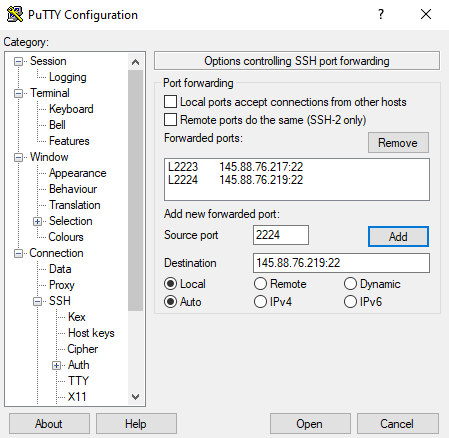
Click on the category “Tunnel” and set a source port and destination for each login node,i.e.,
Then, go back to the category “Session” and make sure to save the new settings for session “alice_gw”. | Click on the category “Tunnel” and set a source port and destination for each login node,i.e.,
Then, go back to the category “Session” and make sure to save the new settings for session “shark_gw”. | |
In order to connect to the login nodes, we need to setup a second session:
Connecting to ALICE is a two step process. | In order to connect to the login nodes, we need to setup a second session:
Connecting to SHARK is a two step process. | |
First, load the session “alice_gw” by clicking on the corresponding name in the list followed byclicking on the button “Load” and the button “Open”. When you connect for the first time, PuTTY will raise a security alert in an overlay window. Confirm the authenticity of the server that you try to connect to by clicking “Accept”. | ||
Next, specify your ALICE user name, confirm with enter. Then, PuTTY will ask for your ALICE user password. Type it in and confirm with enter. For novice users: When you type in your password, you will not see any characters appearing. It will seem as if the line is blank and you have typed nothing in. However, this is not the case. You will have typed in the password. | Next, specify your SHARK user name, confirm with enter. Then, PuTTY will ask for your SHARK user password. Type it in and confirm with enter. For novice users: When you type in your password, you will not see any characters appearing. It will seem as if the line is blank and you have typed nothing in. However, this is not the case. You will have typed in the password. | |
When successful, you should be logged in to the gateway. Keep this session open, but do not do anything further with it. | When successful, you should be logged in to the gateway. Keep this session open, but do not do anything further with it. | |
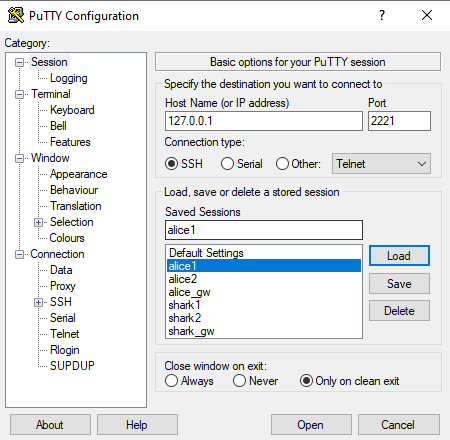
Open a second session to a login node, by loading the settings for “alice1” or “alice2”. When you connect for the first time, PuTTY will raise a security alert in an overlay window. Confirm the authenticity of the server that you try to connect to by clicking “Accept”. | Open a second session to a login node, by loading the settings for “alice1” or “alice2”. When you connect for the first time, PuTTY will raise a security alert in an overlay window. Confirm the authenticity of the server that you try to connect to by clicking “Accept”. | |
Next, specify your ALICE user name, confirm with enter. Then, PuTTY will ask for your ALICE user password. Type it in and confirm with enter. | Next, specify your SHARK user name, confirm with enter. Then, PuTTY will ask for your SHARK user password. Type it in and confirm with enter. | |
Now, you should be connect to one of the login nodes on ALICE. | Now, you should be connect to one of the login nodes on SHARK. |
For logging out, best to type logout in the session for the login node, followed by logout in the session for the gateway.
X2Go
With X2Go, you can get a remote desktop on ALICE. Instructions on how to set X2Go up, can be found here: Getting a remote desktop on ALICE or SHARK with X2Go